
Chameleon Ultra is an RFID emulator that can be used to clone LF (125 kHz) and HF (13.56 MHz) cards. It can read, write, and can be used as a communication analyzer. It supports several cracking methods, and it is also an open source project with a price tag that is incredibly low.
Do you need to test RFID communication? Then take a look at this little device that can be a really big help – Chameleon Ultra.
Chameleon Ultra is in the early stages of development and therefore does not support everything it could potentially do. However, the capabilities of this device are already greater than some competing products, and work is ongoing to implement additional protocols, card support, and cracking methods.
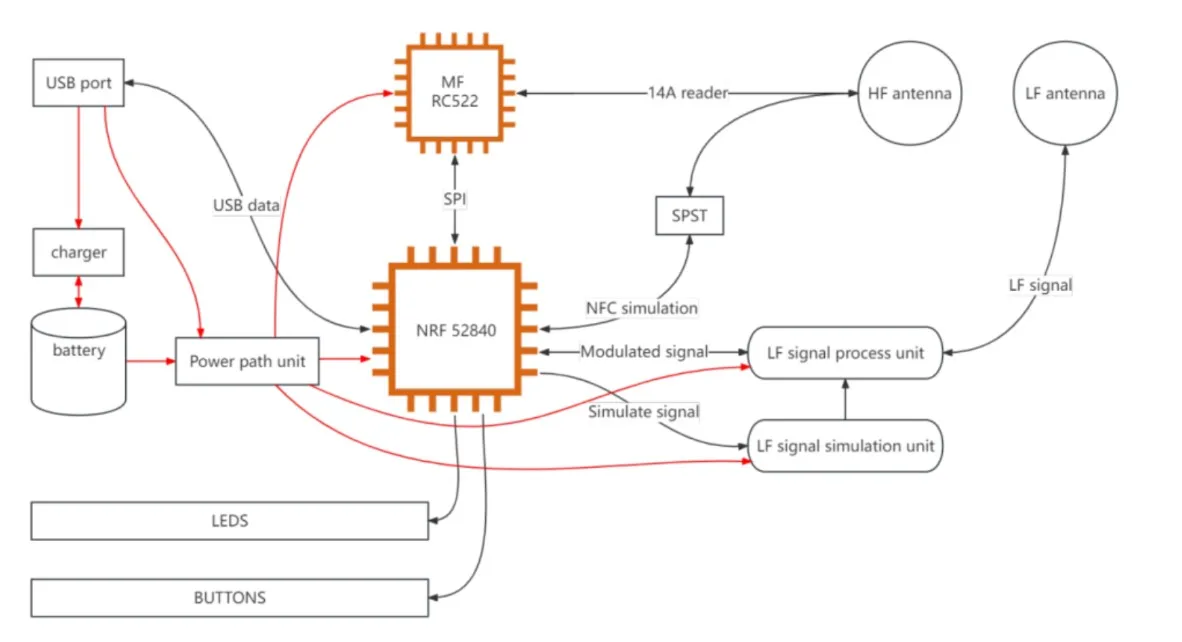
Key features of the Chameleon Ultra device:
- Emulation: The device can simulate a wide range of commonly used RFID chips in both low-frequency (LF – 125 kHz) and high-frequency (HF – 13.56 MHz) spectra. This includes Mifare Classic, NTAG, Ultralight, DESFire, EM410x, HID Prox, Indala, and more.
- Reading and writing: Chameleon Ultra allows reading and writing data to RFID chips, including advanced operations such as modifying UID or changing the card’s content.
- Cloning: The device is capable of quickly and efficiently creating a copy of the original RFID chip. This can be useful for backup purposes or in penetration testing and security analysis of existing systems.
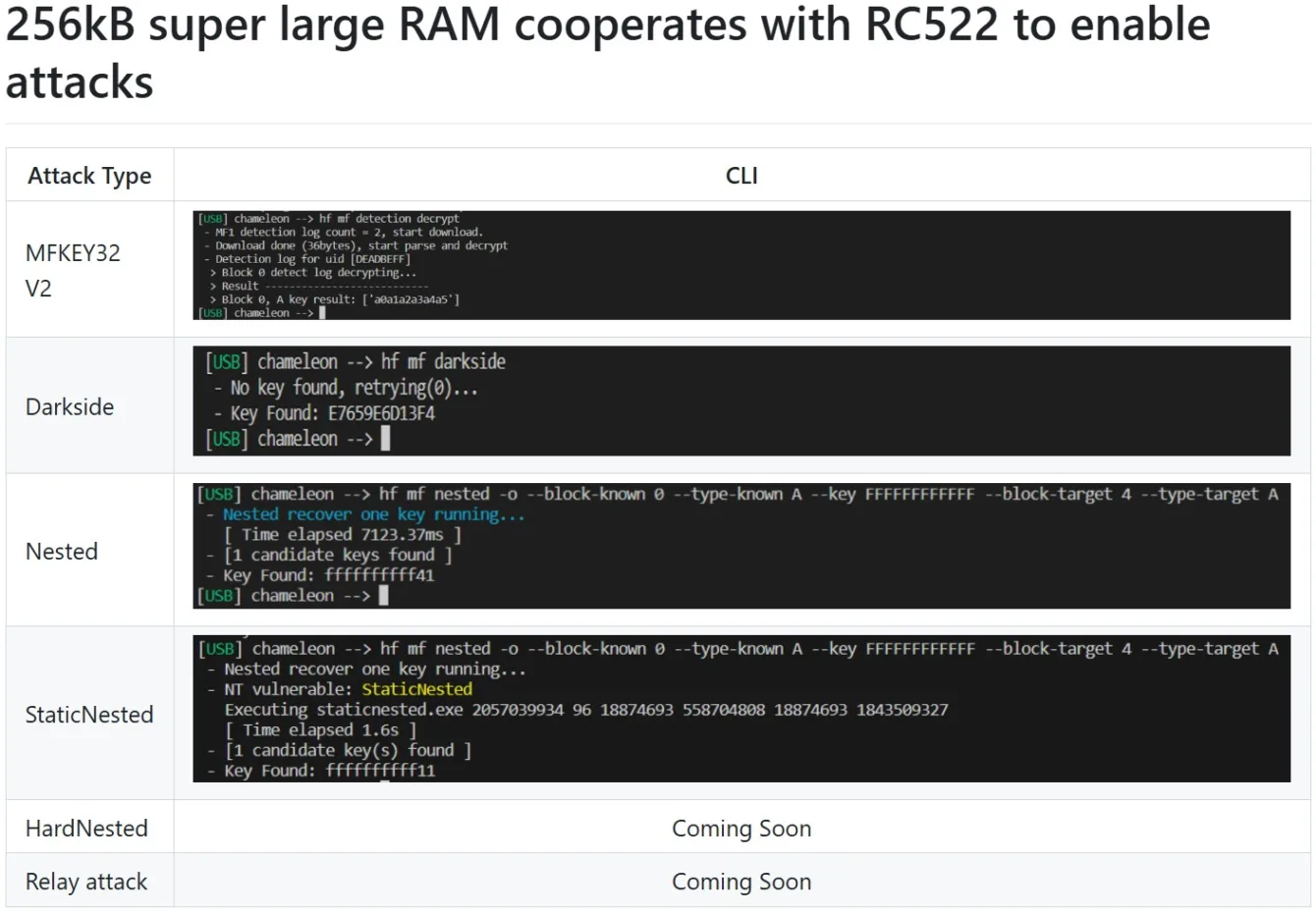
- Cracking: Functionality includes automated attacks on Mifare Classic cards, such as Darkside, Nested, StaticNested, and Hardnested (in preparation), which serve to obtain cryptographic keys and deeper analysis of the card.
- Darkside: Exploits a vulnerability in the MIFARE Classic implementation, where responses to incorrect authentications can be used to decrypt part of the encryption stream, thus obtaining the necessary information to break the key without needing to know the key.
- Nested: Allows obtaining the key of a protected sector by using knowledge of one valid key on the card and a weakness in the random number generator; it retrocalculates a non-zero form of nonce, thus obtaining the keystream.
- StaticNested: A variation of the nested attack that targets cards with a fixed (“static”) value of encrypted nonces, enabling easier offline key retrieval from two authentication sequences.
- HardNested: A modernized variant of the nested attack against “secured” cards with an improved random number generator; it uses a large number of captured nonces and advanced cryptanalysis to find the key without knowledge of previous keys.
- Relay Attack: Facilitates communication between a real card and a reader in real-time (even remotely), so the reader accepts the attacker’s presence as the legitimate card of the victim, without knowing any keys or analyzing the content of the communication.
- Darkside: Exploits a vulnerability in the MIFARE Classic implementation, where responses to incorrect authentications can be used to decrypt part of the encryption stream, thus obtaining the necessary information to break the key without needing to know the key.
Specifications:
- Chipset NRF52840 (32-bit ARM Cortex-M4 @ 64MHz, 256kB RAM, 1MB Flash)
- Support for Bluetooth LE 5.0 for wireless control (mobile app, desktop GUI)
- USB-C interface for programming and firmware updates
- Eight dual-frequency virtual slots (for storing up to 8 HF and 8 LF tags)
- Two programmable buttons, RGB indication, built-in long-lasting Li-Ion battery
- Compact dimensions (approximately 4 × 2.5 × 0.6 cm) and lightweight
Control and software:
Chameleon Ultra can be controlled via a graphical interface (ChameleonUltraGUI), the mobile application Chameleon Ultra GUI (Google Play, iOS) or the command line. For Android, you can also use the mobile application Mtools BLE, which supports not only Chameleon Ultra.
The software is regularly updated and, thanks to a strong community, is constantly being expanded with new features and supported card types. Firmware updates are straightforward and can be performed either via USB or wirelessly over Bluetooth.
Practical applications:
The Chameleon Ultra device is an interesting choice for security experts, penetration testers, developers, and the academic community focused on digital security. And of course, for anyone interested in technology.
Comparison with competing products:
Compared to other devices like the Proxmark3 or Flipper Zero, the Chameleon Ultra stands out particularly in emulation accuracy, versatility, ease of use, and performance, especially when analyzing Mifare Classic. Another advantage is its full openness – firmware, hardware, and software are available under an open source license.
Chameleon Ultra wiki https://github.com/RfidResearchGroup/ChameleonUltra/wiki/technical_whitepaper
Available at https://pajenicko.cz/chameleon-ultra-open-source-rfid-emulator for 999 CZK
If you want to dive deeper into this topic, you might find the Chameleon Ultra DevKit useful https://lab401.com/en-de/products/chameleon-ultra-devkit




